Following my last blog we are still seeing a large amount of Malware on
old & new customer’s computers. Malware
gets its name from the term malicious software, this gets installed onto your computers
with single click of your mouse. You’ve
all heard of Trojans, Spyware, Adware and Randsomware. We would like to help you understand and give
and show some examples.
Typically these customers’ computers do have some free security
software which gives some protection, the issue is its only a taster of the software. They don’t cover anywhere near enough of what
you really need to stay safe while your surfing or even receiving e-mails.
Malware gets onto your computer/mobile device in many ways, however most
of the time you agree to install it or action it to start with.
How many of you read the terms and condition on a program you install?
How many of you install Apps onto you mobiles device just accepting all the
requested App permission it says it needs.
F-Secure has an App to find out what permission you have given on all
you apps, if you are Android go to Google play and search for F-Secure app
permission, or just click
here.
Getting back to Malware, I like to show you some examples of how and
what Malware is, and more to the point what can it do.
Adware: advertising-supported software is the full name. These
are advertising pop ups, through these they get you to click which then will
give you more adware on your computer and will get you to install other fake
software.
Trojans:
Trojans horse is its full name, these install by posing themselves as something
else. These hide themselves and steal data without the user knowing. Trojans do
not spread themselves to other computers, they are injected into your computer
from another program. One way you can
get a Trojans onto your computer is when you use pirated software, or use key
generators to made product codes. You
think you’re getting something for nothing when in fact you are just getting
yourself a stir of trouble. An example
of a Trojan is a Keylogger, this logs the keys you press on your keyboard and
sends them to criminals that then have passwords you typed in, credit cards and
so much more.
Spyware:
This will collect data from your computer much like the keyloggers, they take
information of where you surf and send this without the owners consent to serve
the information for your next popup, these are again 4 classed such as system monitors, trojans, adware, and
tracking cookies
Ransomware:
This has evolved and from all the virus and Malware. I have seen them become
very destructive, and can be very costly even if you have backup of your data
in some cases.
The basic Randsomeware infects your computer stopping
you from using / accessing your computer and demanding you pay before you can sign
on again. Some start-up as you try log
onto you profiles saying you had illegal content on you PC or you been surfing
child porn and even in some case adding these photos on your front page. There were easy removed and nondestructive to
your system, unfortunately these have again become destructive, they start by
stopping programs running even after the virus was removed, having to run
software to correct the windows installations. (See example Fig 1,)
Fig 1.
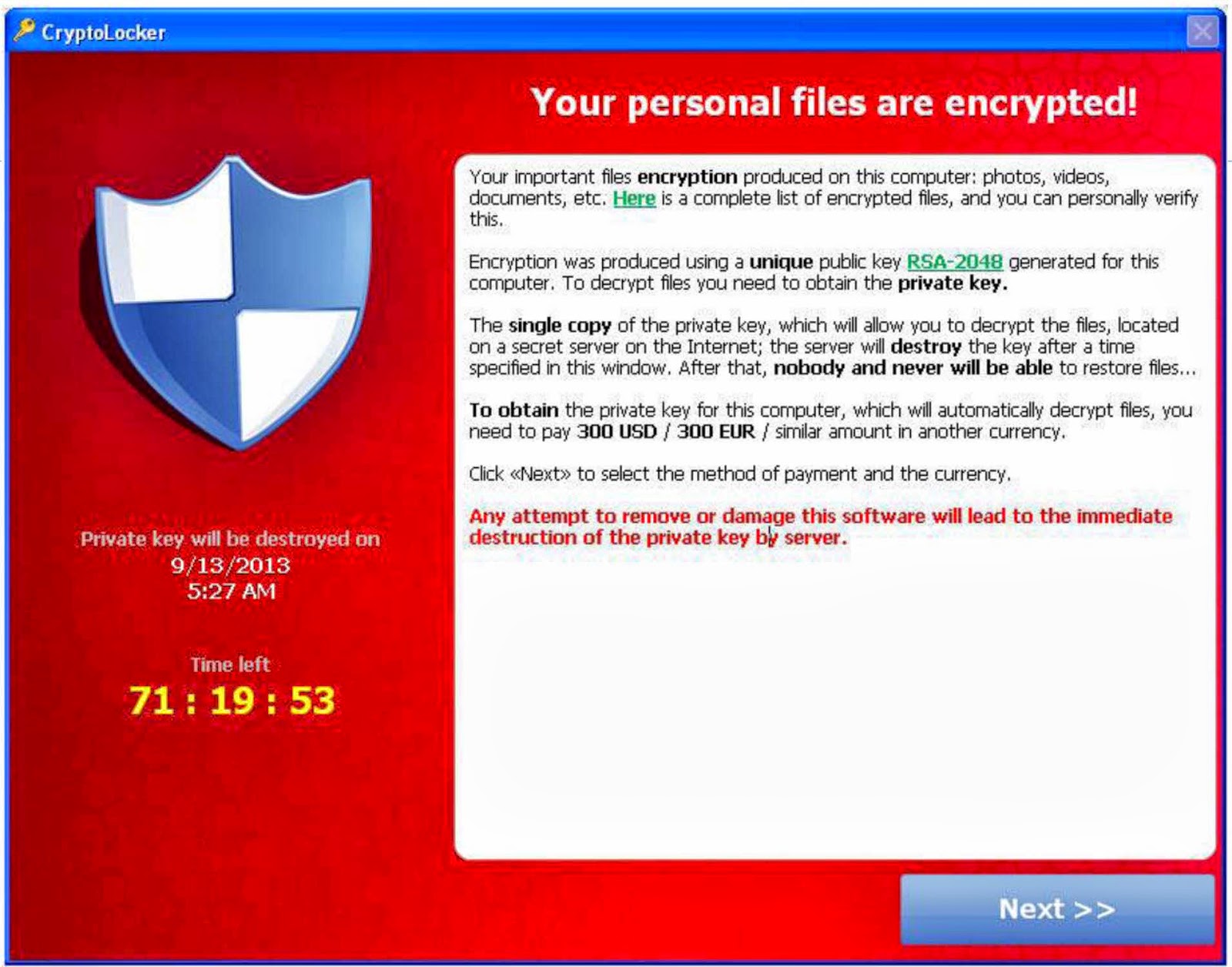
We are now seeing randsomware like cryptolocker. This infects your computer without you knowing
from you clicking an email link or attachment, once on your computer is starts
to encrypted all your personal files approximately 2 days before is shows
itself. It then asks you to make a
payment in bit coins or you will lose all your files. In some cases you can remove the crypto
locker and restore your files from backup.
Problem is most of your backup files are now also encrypted too, most
people sync in the cloud and do no more, there now also encrypted. To top that you are given a time limited to pay
before your files will be unreliable. This then try to also find other
computers on the network and tries to inject itself to other computers, Below
shows images of what randsomware looks like. (Fig 2.)
Fig 2.
Now you know more about what you are trying to protect against, our best advice to anyone is, use an award winning security software to give you the best chance of protecting against these threats.
Speak to Verbo Computers and we share our knowledge of how you can protect yourself with ease.




No comments:
Post a Comment